Zoom is getting some unwanted attention as internet miscreants or mischievous students learn to abuse its open default settings. There have been several reports of “zoombombing” where uninvited guests join a zoom session and share offensive content, including reports from universities.
The biggest defense against these types of attacks is to avoid public posting of Zoom links where they can be accessed by people outside the Penn community. This way someone looking to cause trouble cannot join the meeting just by sniffing out the Zoom link with a Google search.
Additional recommendations include:
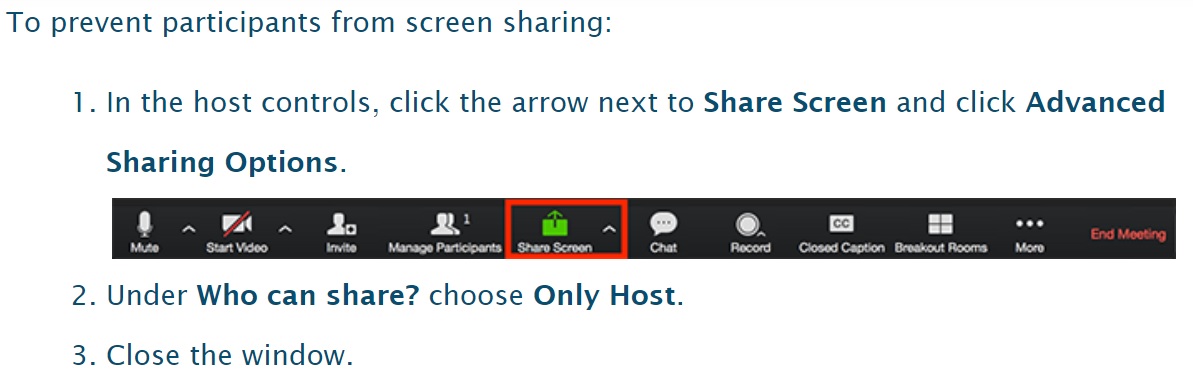
By default, users can share their screen with all participants, allowing a participant to share offensive content with the meeting. With this default setting disabled, users must be authorized by the host before they can share.
Unless needed, disable “file transfer” to avoid participants passing viruses or other malicious content to other participants. File transfer is disabled by default. In case it is enabled:
- Sign in to the Zoom web portal
- Click Settings
- Navigate to the File Transfer option on the Meeting tab and verify that the setting is enabled
- If the setting is enabled, click the Status toggle to disable it
- If a verification dialog displays, choose Turn On to verify the change.
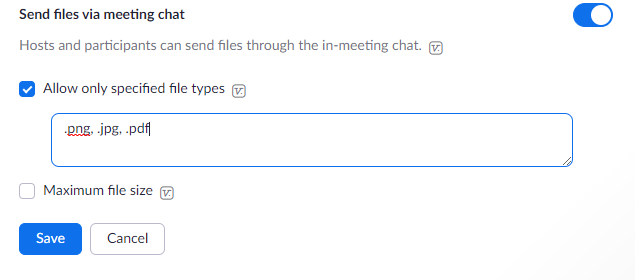
You can limit the file type/extensions you plan to share by taking the following step:
- Sign in to the Zoom Web Portal.
- Click Settings > Meeting-> In Meeting (Basic)
- Navigate to the Send files via meeting chat option.
- Enable Only allow specified file types.
- Enter the allowed file types/extensions, with a comma to separate each.
- Click Save.
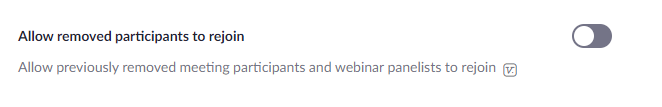
Disable “Allow Removed Participants to Rejoin” so that if a troublemaker is removed from a meeting they cannot simply rejoin:
- Sign in to the Zoom web portal.
- Click Settings.
- Navigate to the Meeting tab and In-Meeting (Basic) and switch off the Allow removed participants to rejoin toggle.
- Be careful when joining personal IDs and Links: Sharing Personal Meeting IDs and personal links can be used to re-join the same meeting room later, which may be unwanted.
- Lock Meeting: To prevent new participants from joining a meeting, the host can lock the meeting after the arrival of attendees by clicking on:
- More at the bottom of the Manage Participants window.
- Select Lock Meeting
- Mute unintentional background noise and Stop disruptive video: The host can mute individual participants unintentional background noise:
- More next the participant's name in the Manage Participants window.
- Click Mute.
- For disruptive video follow the steps to the mute unintentional background but instead of clicking Mute, you can click to Stop a participant video.
- Block annotations to prevent participants from using annotation tools to add information to shared screens.
- Meeting passwords can be employed if there are challenges in restricting access only to the intended participants.
- Limit reuse of access codes: if you've used the same code for many meetings, others will have access to your meetings using the same passcode.
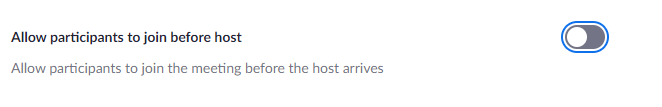
You can disable the option “Allow participants to join before host” to prevent others from using your meeting IDs without you.
- Log in to the Zoom web portal.
- Click Settings
Navigate to Navigate to the Meeting tab and Schedule Meeting and switch off the Allow participants to join before host toggle.