Similar to the way a letter sent through the postal service, an email goes through several hubs, carriers, and routes on its way to your inbox. Unlike a letter, you have the ability to access information about the path an email took before reaching you. This information is contained in a block of data called the email’s headers.
Headers are appended to the email by the various servers that route it to your email provider. Since headers don’t tell you much about the content of an email, your email software doesn’t display them. Header information can tell us about the origin of an email, and about some of the decisions, your email service made when it accepted it from the sender’s email service. As such, it’s important to include an email’s header information when reporting it as suspicious to your IT support staff. Header information makes it easier for the IT support staff to determine whether the message was genuine and help them block other malicious messages.
Unfortunately, most email software does not include an email’s original header information when simply forwarding it. To view an email’s headers:
- To view an email’s headers:
- Open the email message
- Click File on the upper left-hand corner of the message
- Select Properties
- Locate the email headers in the Internet Headers’ box
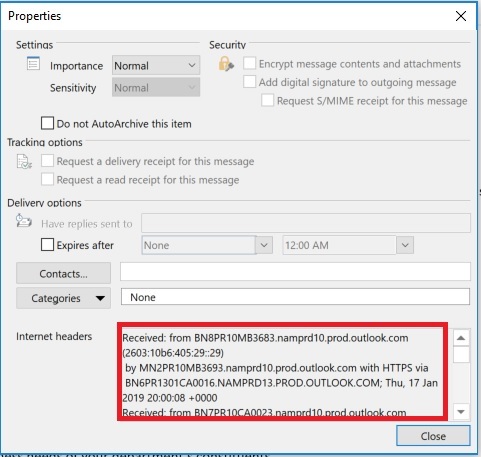
- When reporting an email as phishing or a scam please forward the email as an attachment
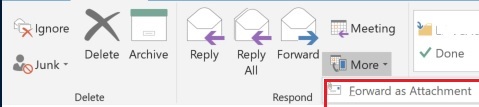
- Click the arrow next to the More button
- Select Forward as Attachment
To view an email’s headers
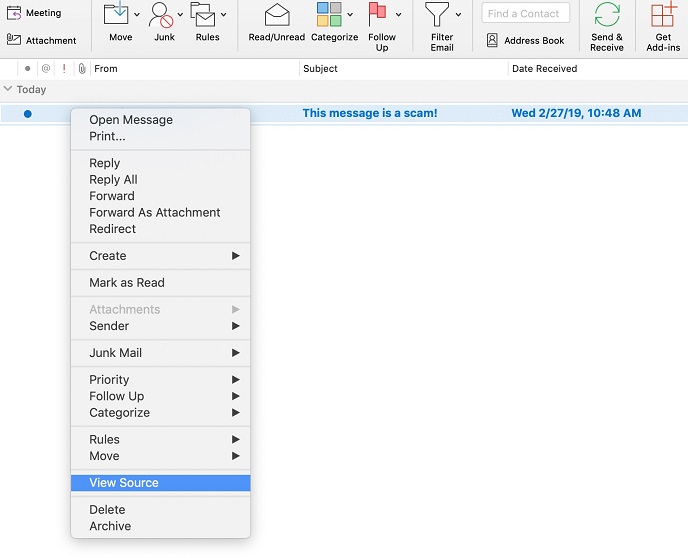
- In the message list in Outlook, right-click on the email’s entry
- Select View source, as shown here:
A plaintext version of the email will appear in a new window in Apple’s TextEdit program, complete with header information.
To report an email as a scam or phishing to your IT Staff, please forward the message as an attachment.
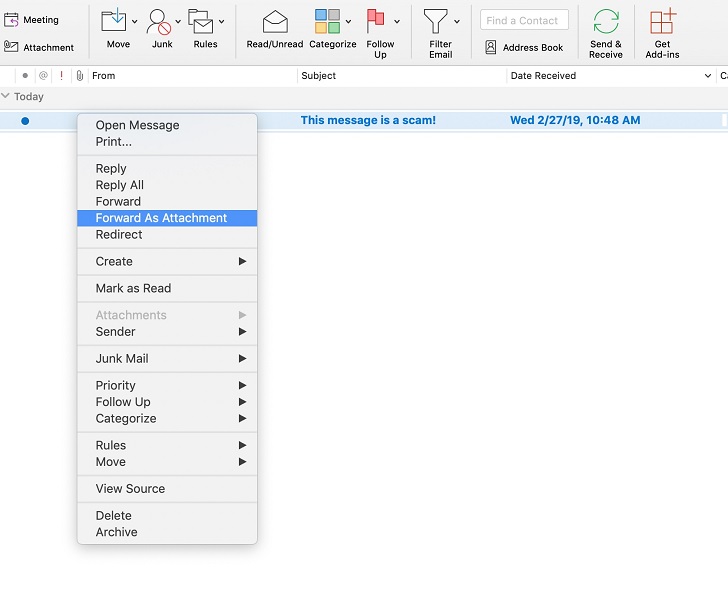
- In the message list in Outlook, right-click on the email’s entry
- Select Forward as Attachment as shown here:
- A new email composition window will appear, with an attachment listed. That attachment is a full copy of the message you’re reporting, including its headers.
- Send the new email to your IT staff.
To view an email’s headers:
- Click on More - the three dots next to the reply button
- Select Show original
- The headers block is displayed in a new window
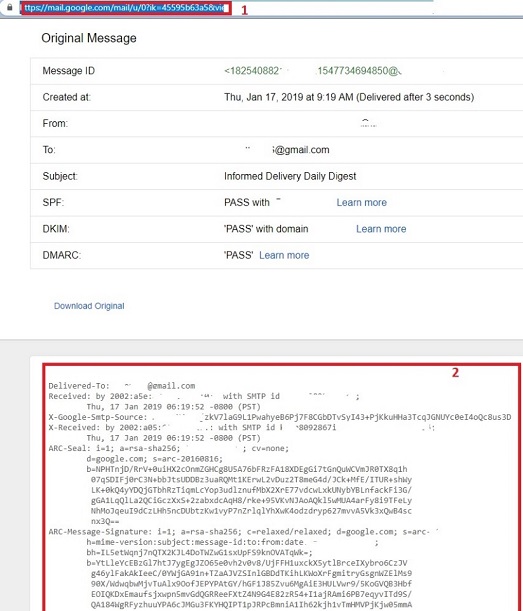
Note: Some information was erased to deidentify the sender and recipient
When reporting an email as phishing or a scam please forward the email as an attachment.
- Open the suspicious email
- Click the More button (three dots next to the reply button)
- Select Download message as shown here:
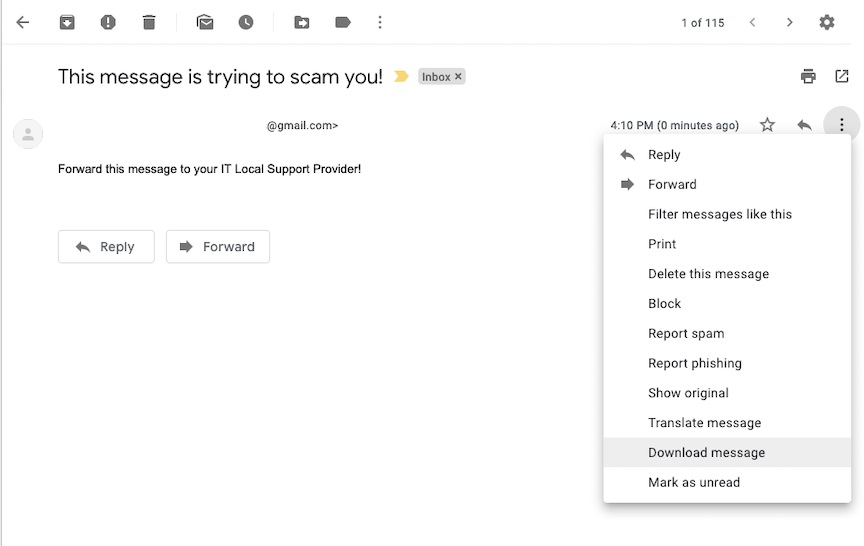
- Compose a new message to your IT staff
- Attach the message you downloaded to the new message and send to your IT staff
To view an email headers
- Click on the email in your inbox to select it
- From the View menu, access Message à Raw Source as shown here:
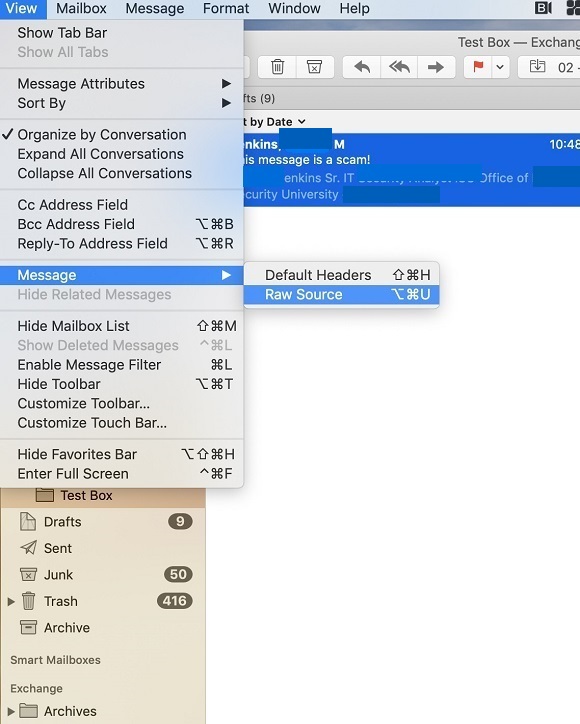
- A new window will open inside the Apple Mail application, showing a plaintext view of the email, complete with headers
When reporting an email as a scam or phishing message to your IT Staff, please forward it as an attachment.
- Right-click on the email in your inbox
- From the resulting menu, select Forward as Attachment as shown here:
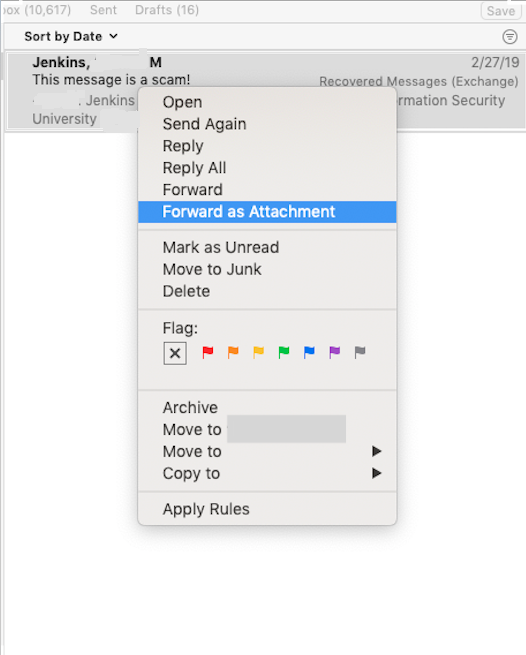
- A new email composition window will appear that will include a copy of the suspicious email as an attachment
- Send the new email to your IT Staff
To view email headers in other email clients visit https://mediatemple.net/community/products/dv/204644060/how-do-i-view-email-headers-for-a-message

